Linux is regarded as one of the most secure operating systems you can use today, that is because of its illustrious security implementation features such as SELinux (Security-Enhanced Linux).
For starters, SELinux is described as a mandatory access control (MAC) security structure executed in the kernel. SELinux offers a means of enforcing some security policies which would otherwise not be effectively implemented by a System Administrator.
When you install RHEL/CentOS or several derivatives, the SELinux feature or service is enabled by default, due to this some applications on your system may not actually support this security mechanism. Therefore, to make such applications function normally, you have to disable or turn off SELinux.
Important: If you don’t want to disable SELinux, then you should read the following articles to implement some mandatory access control on files and services to function properly.
Don’t Miss: Setup Mandatory Access Control with SELinux in Linux
Don’t Miss: Implement Mandatory Access Control with SELinux and AppArmor in Linux
In this how-to guide, we shall walk through steps you can follow to check the status of SELinux and also disable SELinux in CentOS/RHEL and Fedora, in case it is enabled.
How Can I Disable SELinux in Linux
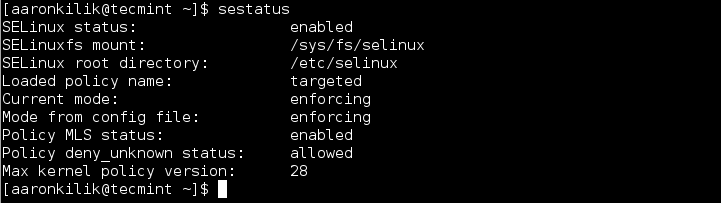
The first thing to do is to check the status of SELinux on your system, and you can do this by running the following command:
$ sestatus
Next, proceed to disabling SELinux on your system, this can be done temporarily or permanently depending on what you want to achieve.
Disable SELinux Temporarily
To disable SELinux temporarily, issue the command below as root:
# echo 0 > /selinux/enforce
Alternatively, you can use the setenforce tool as follows:
# setenforce 0
Else, use the Permissive option instead of 0 as below:
# setenforce Permissive
These methods above will only work until the next reboot, therefore to disable SELinux permanently, move to the next section.
Disable SELinux Permanently
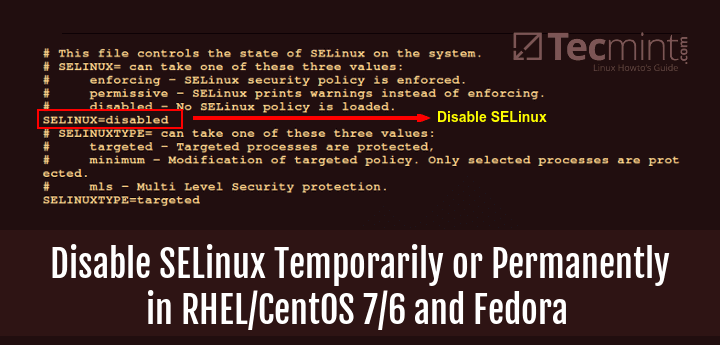
To permanently disable SELinux, use your favorite text editor to open the file /etc/sysconfig/selinux as follows:
# vi /etc/sysconfig/selinux

Then change the directive SELinux=enforcing to SELinux=disabled as shown in the below image.
SELINUX=disabled

Then, save and exit the file, for the changes to take effect, you need to reboot your system and then check the status of SELinux using sestatus command as shown:
$ sestatus

In conclusion, we moved through the simple steps you can follow to disable SELinux on CentOS/RHEL and Fedora. There is nothing much to cover under this topic but additionally, finding out more about SELinux can prove helpful especially for those interested in exploring security features in Linux.



You should take this article and all like it down! You might as well tell your readers to remove their perimeter firewalls down, uninstall their Anti-Virus on Windows, etc.
SELinux is NOT that hard to use and configure. If fact, if you just follow some basic SELinux rules, like keeping all your web server content in /var/www you won’t have any issues.
If you are having an issue use the tools that are given like audit2why and audit2allow. Using audit2allow will fix 99.99999% of your SELinux issues. f you have lots of violations switch to permissive mode (better on a test Machine) and dig through the logs. That’s what competence administrators do!
Advising people to disable SELinux is as stupid as advising them to “just make the user a local administrator, and they will fix it.” on a Windows computer.
Isn’t SELinux part of most distributions by default?
At least now in 2022, eh?
On vagrant VM, I get this for Ubuntu.
What package or repo is needed for SELinux?
@Jim,
SELinux is not part of Debian-based distributions, you need to install it.
When you change /etc/sysconfig/selinux, the SELINUX kernel module still will be loaded, just won’t enforce any policy anymore.
To prevent the whole module from loading we need to add “selinux=0” to the kernel parameters during boot time or execute this command and reboot the system:
This article proved quite useful to me. Thank you!
Only me have that file in /etc/selinux/ instead?
The only thing you left out is why. Why would you do this?
@James
This paragraph states the why bit: “When you install RHEL/CentOS or several derivatives, the SELinux feature or service is enabled by default, due to this, some applications on your system may not actually support this security mechanism. Therefore, to make such applications function normally, you have to disable or turn off SELinux.”