The primary use of computers in any form, whether it’s a mobile phone, personal computer, or a workstation, or a server offering services on the internet, is for the storage and manipulation of data and generation of information to support our daily lives. Paramount in our use of or interaction with computers is privacy and data or information security whether these entities are at rest (in storage) or in transit.
Even as a beginner or an intermediate Linux user, it will serve you right to always use your laptop, workstation, or VPS in the cloud with security in mind. We have prepared a list of features security features and tools for you to get started with understanding and practicing security on any Linux operating system.
We start with file permissions.
1. Linux File Permissions
In Unix-like operating systems such as Linux systems, everything is a file. So file permissions are the bedrock of security in the Linux file system.
For each file in a Linux system, permissions are assigned to these three permission classes: the owner of the file, the group owner, and others. And there are three basic permissions: read, write, and execute. Each permission class may have all or none of the permissions on a file.
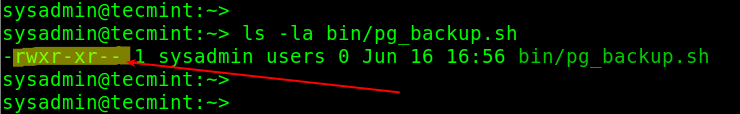
To list the permissions of a file, you can use the ls command with the -la flags as follows.
$ ls -la bin/pg_backup.sh
To learn more about file permissions, check out these guides:
- How to Manage Users & Groups, File Permissions & Attributes in Linux
- How to Copy File Permissions and Ownership to Another File in Linux
- Learn Basic File Management Commands in Linux
2. Sudo Command
The sudo command is a crucial command on Linux systems. It allows you to run other commands with the privileges of another user, normally as a user who has a higher level of authorization on the system. For example the super system user or root user. The user invoking sudo is usually prompted to enter their password to complete the process.
Most Linux distributions come with the sudo command installed and usually, the default administrative user created during system installation is configured to invoke sudo. On some distros, you can manually configure a user account to invoke the sudo command.
It allows a user to perform tasks such as installing or removing packages, creating other user accounts, accessing files and directories owned by the root user, and so much more. But it all depends on what a system administrator has configured a sudo user account to perform on a Linux system.
For more information about the sudo command, check out these guides:
- How to Run Sudo Command Without Entering a Password in Linux
- 10 Useful Sudoers Configurations for Setting Sudo in Linux
- The Difference Between Su and Sudo in Linux
- How to Create a New Sudo User on Ubuntu
Ultimately, you can read its man page by running the following command:
$ man sudo
3. Su Command
The primary purpose of the su command is to allow a privileged user to switch to another user’s account. Ideally, it will enable one user account to run commands with a substitute user and group ID, by providing the password of the substitute user. In most cases, it can be invoked with the sudo command to switch to the root user account to execute some administrative tasks.
To understand this command better, read its man page:
$ man su
4. Data Backup and Recovery Tools in Linux
Backing up data is a traditional way of ensuring data security. Therefore the use of backup tools goes without saying. To prevent data loss when you lose a computer or a disaster occurs, you must always keep a backup of your critical data either locally or preferably in the cloud. Backup tools go hand in hand with data recovery tools.
There are so many data backup tools you can leverage on Linux distros. Most if not all distros come by default with backup and recovery tools. Simply search for a backup tool via the system menu and learn how to use it.
Here are some useful Linux backup tools you can get started with:
- The 5 Best Graphical Backup Tools for Ubuntu and Linux Mint
- fwbackups – A Feature-rich Backup Program for Linux
- mintBackup – A Simple Backup and Restore Tool for Linux Mint
- rdiff-backup – A Remote Incremental Backup Tool for Linux
- Tomb – A File Encryption and Personal Backup Tool for Linux
- System Tar and Restore – A Versatile Backup Script for Linux
- How to Create Bandwidth-efficient Backups Using Duplicity in Linux
- Rsnapshot – A Local/Remote Backup Tool for Linux
- How to Sync Two Apache Web Servers/Websites Using Rsync
- How to Auto Backup Files to USB Media When Connected
5. ClamAV
Another key security tool for Linux systems is ClamAV, which is an open-source, multi-platform antivirus engine for detecting trojans, viruses, malware, and other malicious threats in files. It runs on Linux systems, Windows, and Mac OS X, as well as other Unix-like systems.
There are many other antivirus software you can use on Linux systems, read more in this article – 8 Best Free Anti-Virus Programs for Linux.
6. OpenSSH
As you advance in your Linux journey, you will reach a point when you have to start interacting with remote Linux systems, for example, a VPS in the cloud. The most secure and highly recommended means to achieve this is through SSH (short for Secure Shell).
OpenSSH is a widely-used client-server program for remote access. A client (known as ssh) runs on your local machine(s) and establishes a secure communication tunnel with the server (known as sshd or ssh daemon) that runs as a service (or continuously) on the remote computer, listening to access requests.
It supports various methods of authentication including passwords (not recommended) and public key authentication (highly recommended).
The following are some useful guides about ssh:
- How to Secure and Harden OpenSSH Server
- How to Setup SSH Passwordless Login in Linux
- How to Setup SSH Passwordless Login in Debian
- How to Configure SSH Passwordless Login in RHEL 9
- How to Configure SSH Passwordless Login in openSUSE
- Setup Passwordless SSH Login for Multiple Remote Servers Using Script
There are several other remote access tools that you will learn about, you can start here: 11 Best Tools to Access Remote Linux Desktop.
7. Data Encryption/Decryption Tools
Encryption is a modern data security principle. It allows you to conceal data or information in such a way that it appears random (and meaningless) and can only be accessed by authorized parties only. It involves the use of cryptography algorithms to encrypt data and secret keys to decrypt it.
You can encrypt data at rest (when is it stored on disk) or in transit (for example between a user’s browser and a server holding files of a website on the internet).
There are several encryption tools on Linux operating systems to use especially for disk encryption. A vast majority of modern backup tools also offer data encryption capabilities for extra security.
Check out:
- Top 5 Software Tools for Linux with Data Encryption
- Duplicity – Create Encrypted Incremental Backups in Linux
- How to Encrypt Full Disk While Installing Ubuntu
8. Keeping Your Linux System Up-to-date
Additionally, not a feature or a tool, but a best practice. Always keep any software installed on your computer up-to-date, right from the operating system. Latest software updates usually ship with some fixes for bugs that could potentially expose your Linux machine to the threat from cybercriminals. You can mitigate software-related security risks by always installing the latest updates available.
That’s it! Take your time and explore these features and tools in-depth, you can get back to us concerning this topic via the comment form below. If you are a Linux expert, add your voice, and let us know what you think of this post, all in the comments.