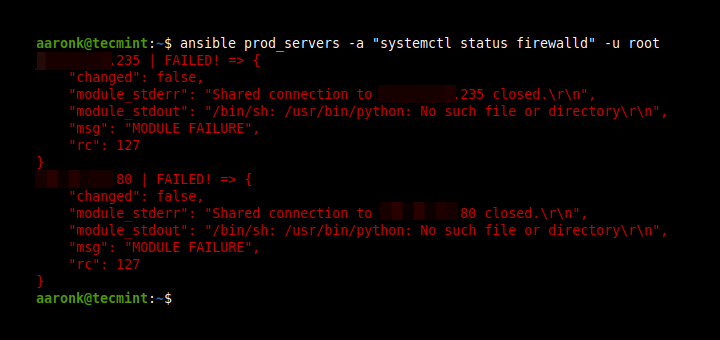
As you go about using Ansible, you may be required to key in some confidential or secret information in playbooks. This includes SSH private and public keys, passwords, and SSL certificates to mention just a few. As we already know, its bad practice to save this sensitive information in plain text for obvious reasons. This information requires to be kept under lock and key because we can only imagine what would happen if hackers or unauthorized users got a hold of it.
Thankfully, Ansible provides us with a handy feature known as Ansible Vault. As the name suggests, the Ansible Vault helps secure vital secret information as we have discussed earlier. Ansible Vault can encrypt variables, or even entire files and YAML playbooks as we shall later demonstrate. It’s a very handy and user-friendly tool that requires the same password when encrypting and decrypting files.
Let’s now dive in and have an overview of the various operations that can be carried out using Ansible vault.
How to Create an Encrypted File in Ansible
If you want to create an encrypted Playbook file simply use the ansible-vault create command and provide the filename as shown.
# ansible-vault create filename
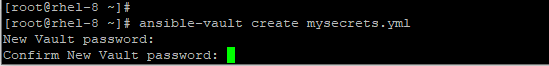
For example, to create an encrypted file mysecrets.yml execute the command.
# ansible-vault create mysecrets.yml
You will thereafter be prompted for a password, and after confirming it, a new window will open using the vi editor where you can begin writing your plays.
Below is a sample of some information. Once you are done simply save and exit the playbook. And that’s just about it when creating an encrypted file.
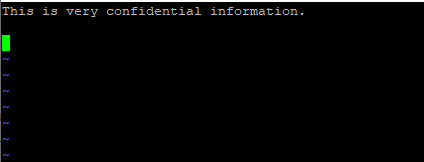
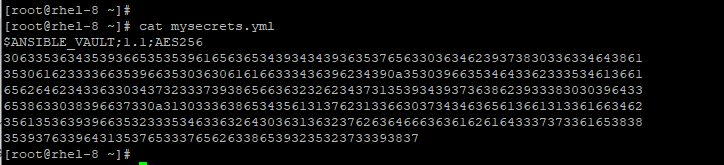
To verify the file encryption, use the cat command as shown.
# cat mysecrets.yml
How to View an Encrypted File in Ansible
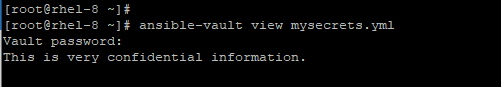
If you want to view an encrypted file, simply pass the ansible-vault view command as shown below.
# ansible-vault view mysecrets.yml
Once again, you will be prompted for a password. Once again, you will have access to your information.
How to Edit an Encrypted File in Ansible
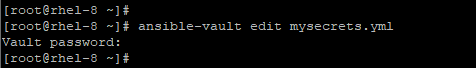
To make changes to an encrypted file use the ansible-vault edit command as shown.
# ansible-vault edit mysecrets.yml
As always, provide the password and thereafter proceed editing the file.
After you are done editing, save and exit the vim editor.
How to Change Ansible Vault Password
In case you feel the need to change the Ansible vault password, you can easily do so using the ansible-vault rekey command as shown below.
# ansible-vault rekey mysecrets.yml
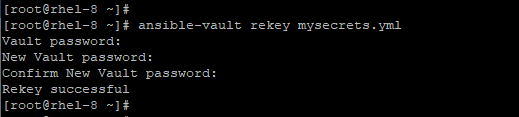
This prompts you for the vault password and later requests you to enter the new password and later confirm it.
How to Encrypt an Unencrypted File in Ansible
Suppose you want to encrypt an unencrypted file, you can do so by running the ansible-vault encrypt command as shown.
# ansible-vault encrypt classified.txt
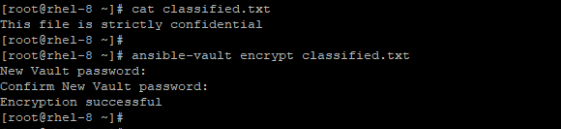
You can later view the file using the cat command as indicated below.
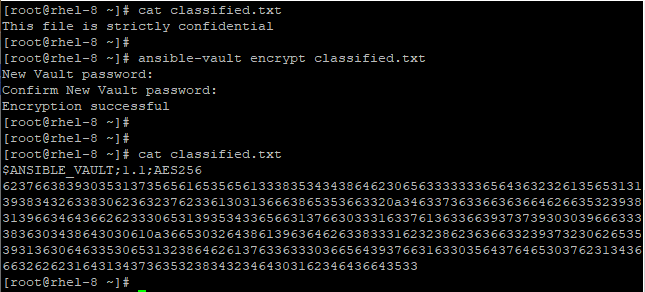
How to Decrypt an Encrypted File
To view the contents of an encrypted file, simply decrypt the file using the ansible-vault encrypt as illustrated in the example below.
# ansible-vault decrypt classified.txt
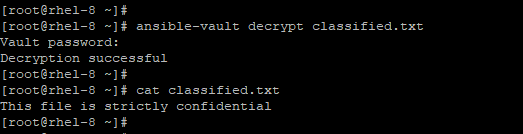
How to Encrypt Specific Variables in Ansible
Additionally, Ansible vault grants you the ability to encrypt certain variables. This is done using the ansible-vault encrypt_string command as shown.
# ansible-vault encrypt_string
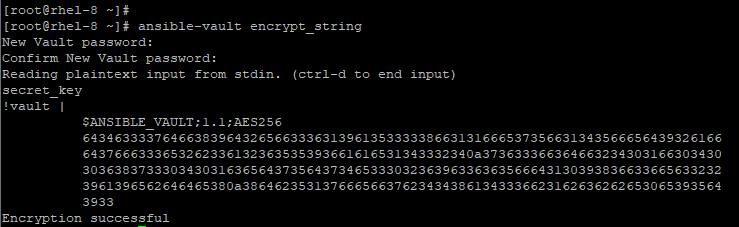
Ansible vault will prompt you for the password and later require you to confirm it. Next, type the string value that you want to encrypt. Finally, press ctrl + d. Thereafter, you can begin assigning the encrypted value in a playbook.
This can be achieved in a single line as shown below.
# ansible-vault encrypt_string 'string' --name 'variable_name'
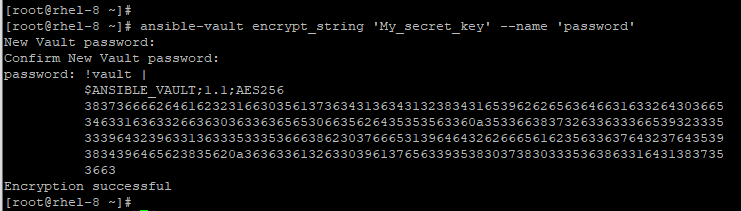
How to Decrypt a Playbook File During Runtime
If you have a playbook file and want to decrypt it during runtime, use the --ask-vault-pass option as illustrated.
# ansible-playbook deploy.yml --ask-vault-pass

This decrypts all the files that are used in the playbook provided that they were encrypted using the same password.
The password prompts can be annoying at times. These prompts make automation untenable, especially when automation is key. To streamline the process of decrypting playbooks during runtime, it’s recommended to have a separate password file that contains the Ansible vault password. This file can then be passed during runtime as shown.
# ansible-playbook deploy.yml --vault-password-file /home/tecmint/vault_pass.txt
This brings us to the conclusion of this topic and the Ansible automation series. We hope that the tutorials have infused some useful knowledge on how you can automate tasks across multiple servers from one central system.