The su command is a special Linux command that allows you to run a command as another user and group. It also allows you to switch to the root account (if run without any arguments) or another specified user account.
All users by default are allowed to access the su command. But as a system administrator, you can disable su access for a user or group of users, using the sudoers file as explained below.
The sudoers file drives the sudo security policy plugin which determines a user’s sudo privileges. The sudo command allows users to run programs with the security privileges of another user (by default, as the root user).
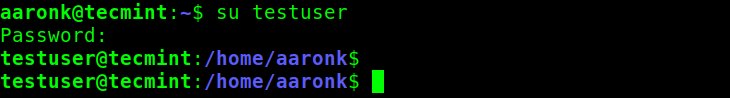
To switch to another user account, a user can run the su command from their current login session as shown. In this example, the user aaronk is switching to a testuser account. The user aaronk will be prompted to enter the password for the testuser account:
$ su testuser
To switch to the root account, a user must have the root password or have privileges to invoke the sudo command. In other words, the user must exist in the sudoers file. In this example, the user aaronk (a sudo user) is switching to the root account.
After invoking sudo, the user aaronk is prompted to enter his or her password, if it’s valid, the user is granted access to an interactive shell as root:
$ sudo su

Disable su Access for a Sudo User
To disable su access for a sudo user for example the aaronk user above, first, back up the original sudoers file located at /etc/sudoers as follows:
$ sudo cp /etc/sudoers /etc/sudoers.bak
Then open the sudoers file using the following command. Note that it’s not recommended to edit the sudoers file by hand, always use the visudo command:
$ sudo visudo
Under the section of command aliases, create the following alias:
Cmnd_Alias DISABLE_SU = /bin/su
Then add the following line at the end of the file, replace the username aaronk with the user you wish to disable su access for:
aaronk ALL=(ALL) NOPASSWD: ALL, !DISABLE_SU
Save the file and close it.
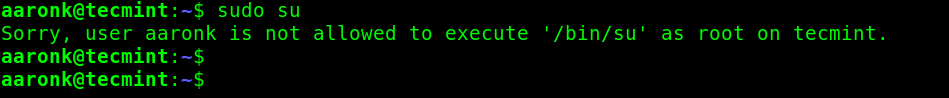
Then test to verify that setup is working as follows. The system should return an error message like this: “Sorry, user aaronk is not allowed to execute ‘/bin/su’ as root on tecmint.”.
$ sudo su
Disable su Access for a Group of Sudo Users
You can also disable su access for a group of sudo users. For example to disable su access for all users in the group admin, modify the line:
%admin ALL=(ALL) ALL
to this:
%admin ALL=(ALL) ALL, !DISABLE_SU
Save the file and close it.
To add a user to the admin group, run the usermod command (replace username with the actual user):
$ sudo usermod -aG admin username
For more information about the su, sudo and sudoers, check their man pages:
$ man su $ man sudo $ man sudoers



But if the user aaronk knows the root password he can still do a “su – root” (without sudo) to gain root access, right?
@Sven,
Yes, you are right – If a user knows the root password, he can indeed gain access to the root account on a system.
In the last code block, you have “sodoers” misspelled as “sudeors“…
Or if I could spell right “sudoers” not “sodoers” ;-)