Developed by Puppet Lans, Puppet is an open-source configuration management tool used for automating and centralizing the configuration of infrastructure such as servers just like Ansible and Chef. It helps the simple execution of repetitive tasks which would otherwise be cumbersome and time-consuming.
Puppet adopts a client-server architecture and comprises the following salient aspects.
- Puppet Master/Server – This node contains all the configuration required to manage client nodes on which the puppet slave is installed.
- Puppet Slave – These are the managed client nodes in your environment. All slaves are managed by the Puppet master and have the Puppet agent installed and running.
- PuppetDB – This is a database that stores all the data generated by Puppet.
In this guide, we will demonstrate how to install Puppet Master and Agent in RHEL-based distributions such as CentOS, Fedora, Rocky, and AlmaLinux.
Lab Environment Setup
Puppet Master Node with IP 139.144.20.170 - Rocky Linux 8 Puppet Slave with IP 45.79.206.178 - Ubuntu 22.04
Table of Contents
Step 1: Configure Hostname in Puppet Master and Slave
To get off the ground, log into your system and upgrade the software packages using the dnf command as follows.
$ sudo dnf update -y
Next, configure a hostname for your nodes, which will be valuable along the way as you set up Puppet on your system.
For Puppet Master
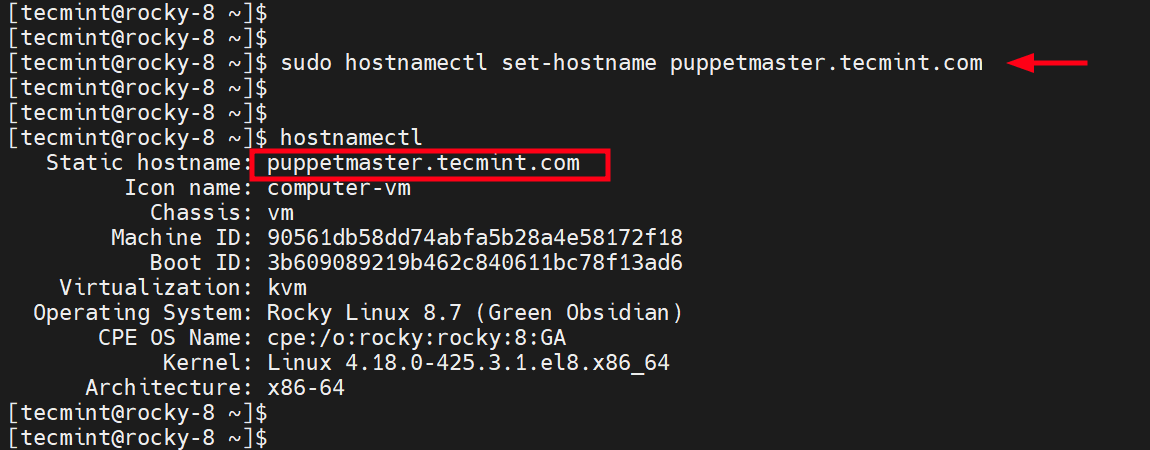
$ sudo hostnamectl set-hostname puppetmaster.tecmint.com
For Puppet Slave
$ sudo hostnamectl set-hostname puppet-agent
Confirm the new hostname using the hostnamectl command:
$ hostnamectl
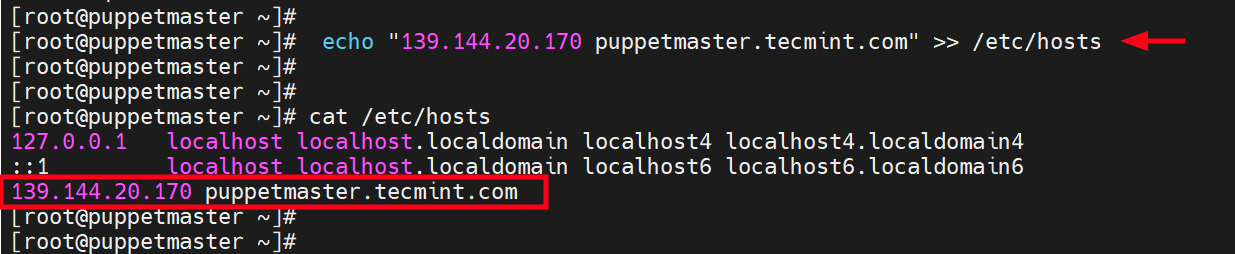
Next, update the /etc/hosts file for both systems with the hostname and DNS records as shown.
Switch to the root user.
$ su -
Next, update the /etc/hosts file with the IP address and hostname or FQDN of your system.
For Puppet Master
# echo "139.144.20.170 puppetmaster.tecmint.com" >> /etc/hosts
For Puppet Slave
# echo "45.79.206.178 puppet-agent" >> /etc/hosts
Once the hostnames and DNS records have been set up, proceed with the next step.
Step 2: Add Puppet Repository on Puppet Master (Rocky Linux)
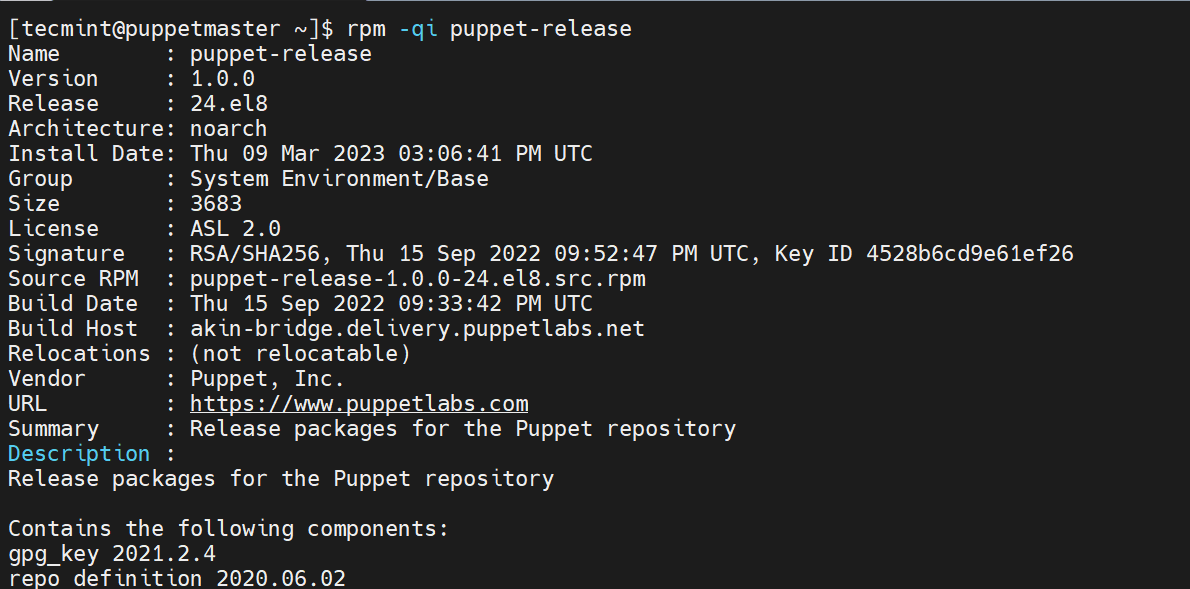
To install Puppet, we need to add its repository to the system. To do so, run the following command.
$ sudo dnf install https://yum.puppet.com/puppet-release-el-8.noarch.rpm -y
![Add Puppet Repository on Rocky Linux [Puppet Master]](https://www.tecmint.com/wp-content/uploads/2014/10/Add-Puppet-Repository-on-Rocky-Linux.png)
$ rpm -qi puppet-release
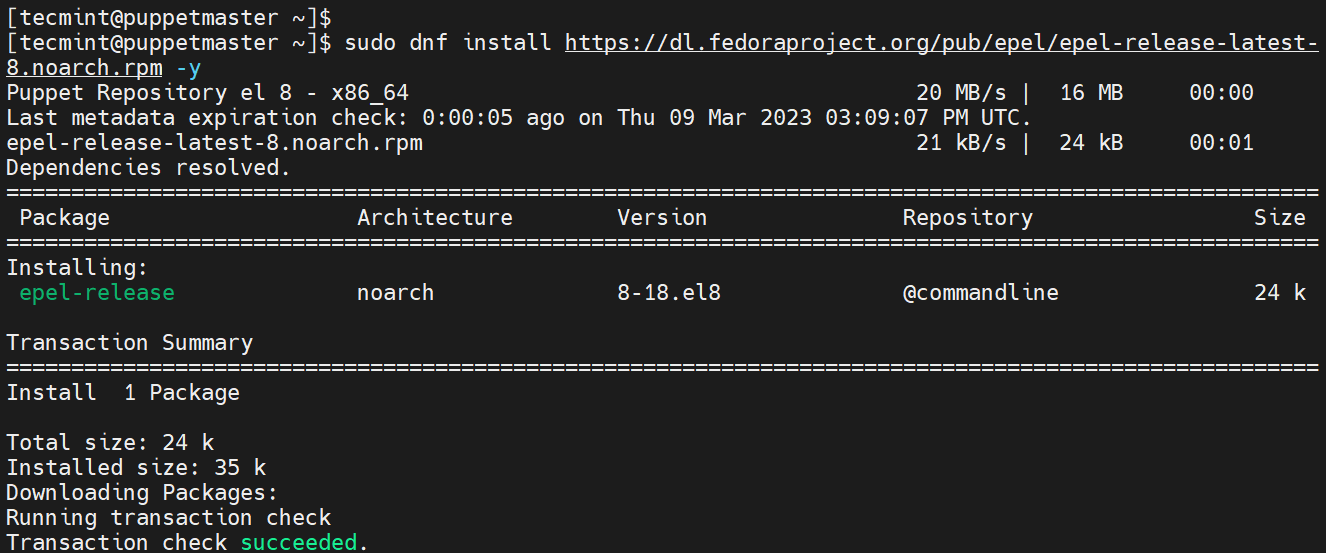
In addition, ensure to also add the EPEL repository as shown.
$ sudo dnf install https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rpm -y
Next, enable the Powertools repository which provides developer tools and libraries. The repository also provides a host of packages that are needed as dependencies when installing other applications.
$ sudo dnf config-manager --set-enabled powertools
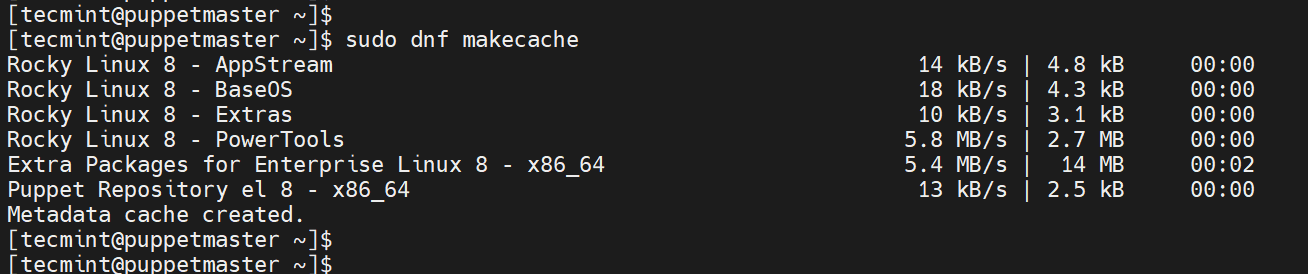
To ensure the cache is fully up to date with all metadata in place, build the cache as shown.
$ sudo dnf makecache
Step 3: Install Puppet on Puppet Master (Rocky Linux)
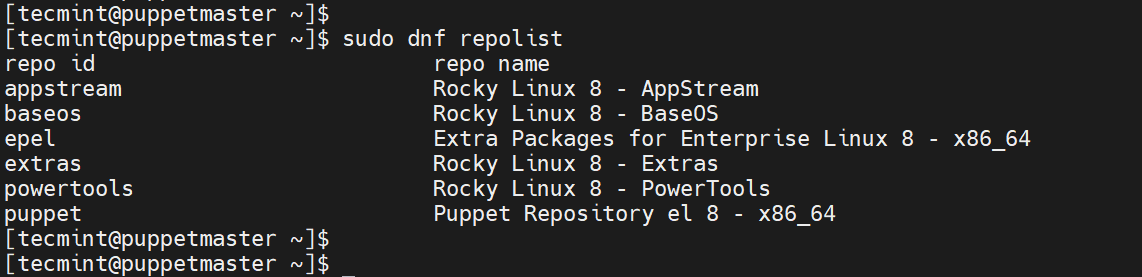
Before you install Puppet, ensure that all the required repositories have been enabled as follows.
$ sudo dnf repolist
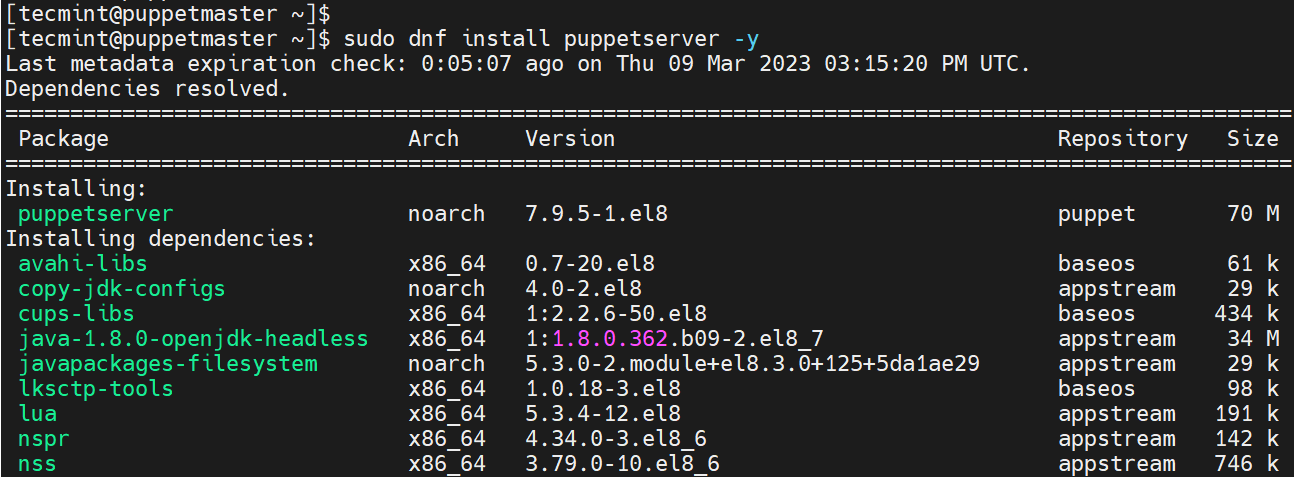
Next, install Puppet Server as follows.
$ sudo dnf install puppetserver -y
The command installs a host of packages including Pupper Server and Agent, Java OpenJDK, Lua, NSS, and many more. Below is the command output.
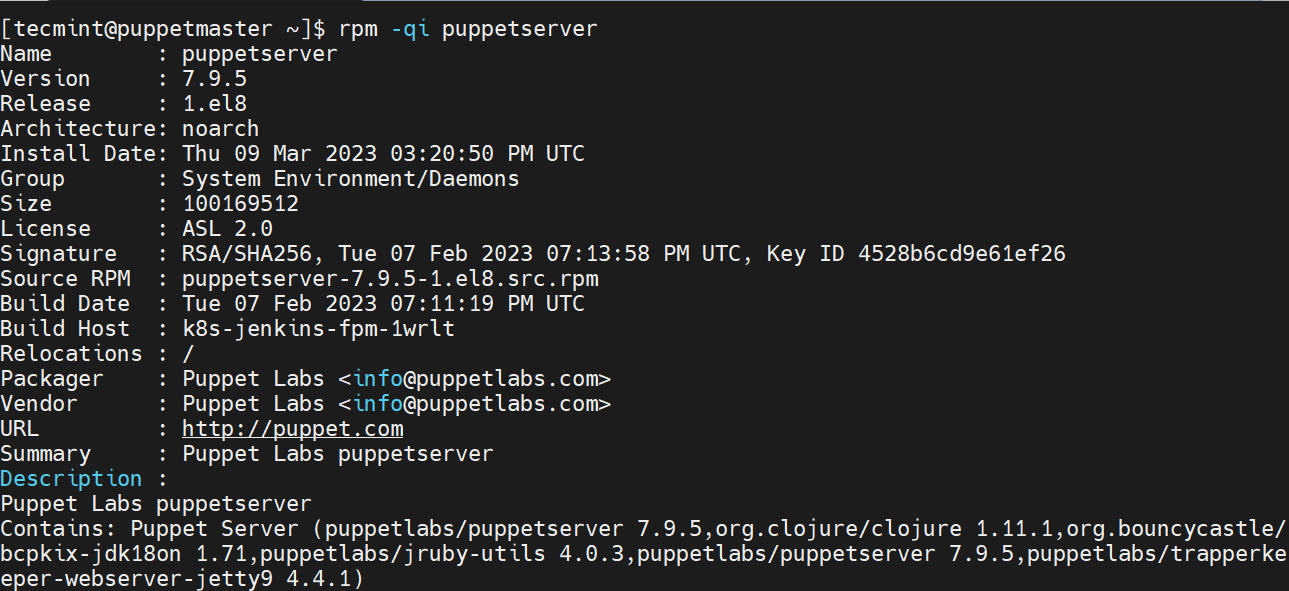
To confirm that the Pupper Server has been installed, run the command:
$ rpm -qi puppetserver
The command prints out detailed information such as name, version, release, architecture and install date to mention a few.
Step 4: Configure Puppet Master Server (Rocky Linux)
Once Puppet Server is installed, the next step is to configure it. Therefore, access the main configuration file for Puppet as shown.
$ sudo vim /etc/puppetlabs/puppet/puppet.conf
Under the [server] section add the DNS entry as shown.
dns_alt_names=puppetmaster.tecmint.com,puppetmaster,puppetserver
In addition, add the [main] section as follows, where puppetmaster.tecmint.com is the FQDN or hostname of your puppet server.
[main] certname = puppetmaster.tecmint.com server = puppetmaster.tecmint.com environment = production runinterval = 1h
This is what our configuration looks like.
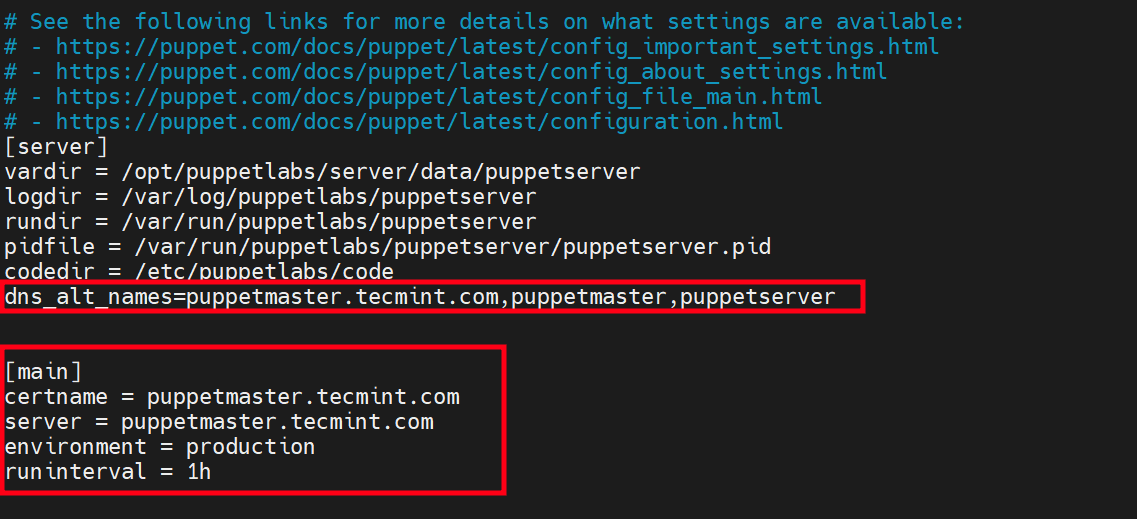
Save the changes and exit the configuration file.
Step 5: Configure JVM Memory Allocation (Optional)
By default, 2GB of JAVA memory is allocated to Puppet Master Server. If your system doesn’t have sufficient memory, you can edit the server configuration file and assign a lower value such as 1GB.
Therefore, access the configuration file.
$ sudo vim /etc/sysconfig/puppetserver
Locate these arguments: -Xms2g -Xmx2g and change 2g to 1g (means 1GB).
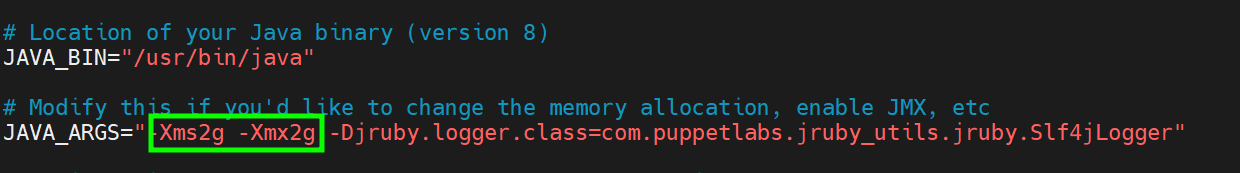
Save the changes and exit the configuration file.
Step 6: Start and Enable Puppet Server
After making all the required changes, start the Puppet Server service as shown.
$ sudo systemctl start puppetserver
Then enable the service to start on boot time or system startup.
$ sudo systemctl enable puppetserver
To verify that the Puppet server is running, execute the command:
$ sudo systemctl status puppetserver
The following output confirms that the Puppet server is running.
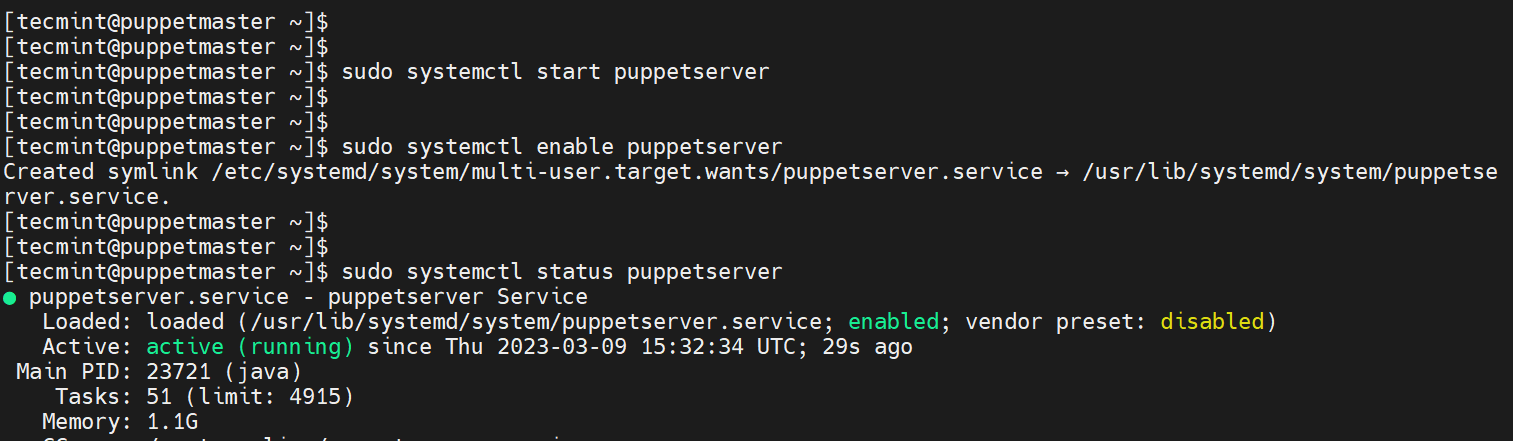
Step 7: Start and Enable Puppet Agent
The installation of Puppet Server also installs the agent as well. However, the agent does not start automatically, and you must do it manually.
To start the puppet agent, run the command.
$ sudo systemctl start puppet
Also, consider enabling the agent to start on boot.
$ sudo systemctl enable puppet
Now, verify if the agent is active and running by running the following command.
$ sudo systemctl status puppet
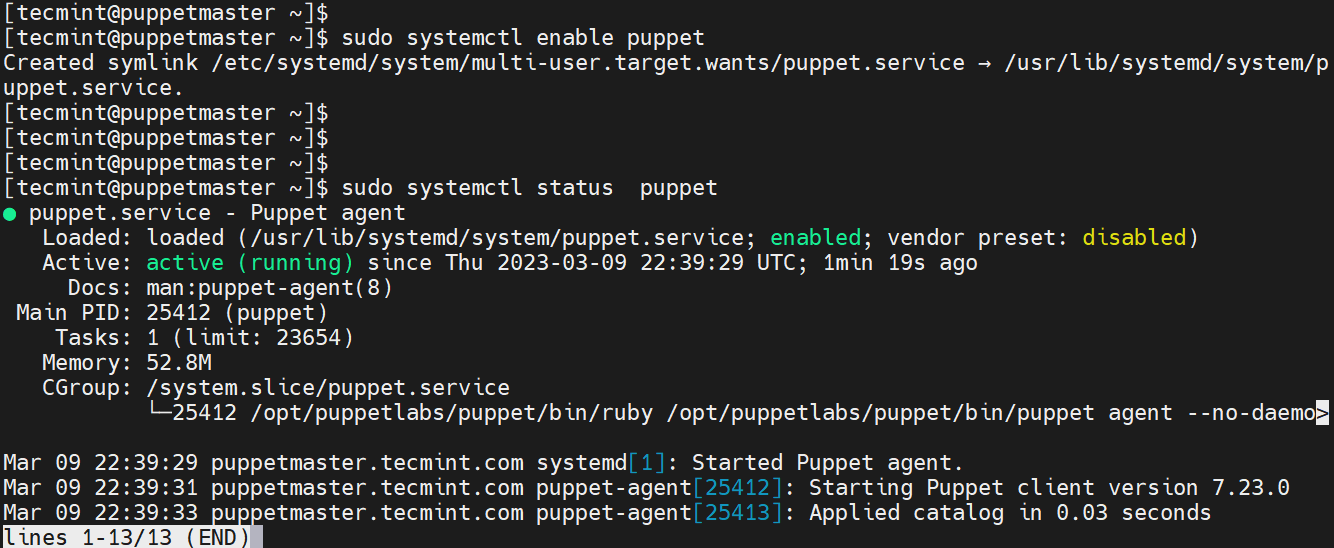
Step 8: Allow Puppet Service in Firewall
Another thing you need to consider is to allow the Puppet service across the firewall so that the server can be accessed over the network.
To do so, run the following commands.
$ sudo firewall-cmd --add-service=puppetmaster --permanent $ sudo firewall-cmd --reload
Step 9: Add Puppet Binary Folder to $PATH
Puppet binaries are located in /opt/puppetlabs/bin. At the time of writing this guide, the directory is already placed in the $PATH.
To confirm this, run the printenv command as shown.
$ printenv | grep puppetlabs
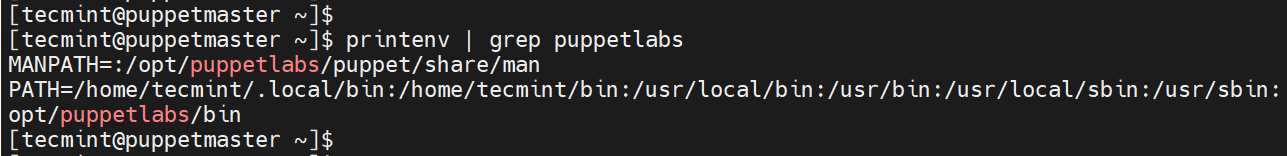
You can also verify that as shown.
$ which puppet /opt/puppetlabs/bin/puppet
If for some reason Puppet is not added to $PATH, switch to the root user
$ su -
Then run the following commands to add it to $PATH.
# echo 'export PATH=$PATH:/opt/puppetlabs/bin' | tee -a ~/.bashrc # source ~/.bashrc
Step 10: Verify Puppet Server Using Puppet Client
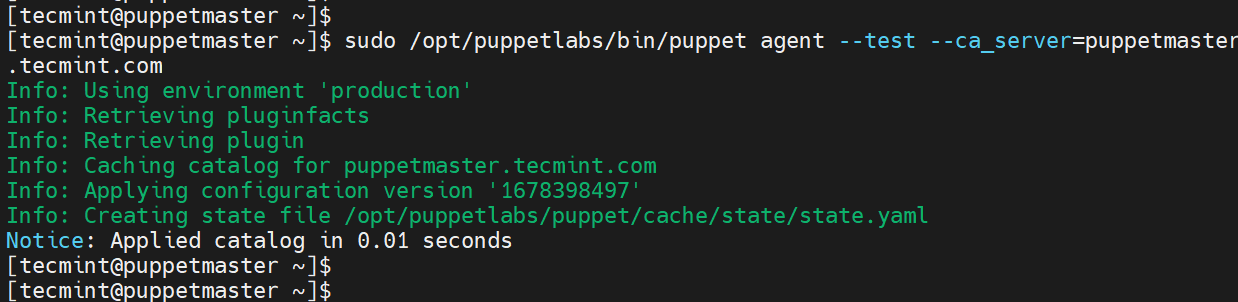
To confirm that the Puppet server is running as expected, run the command:
$ sudo /opt/puppetlabs/bin/puppet agent --test --ca_server=puppetmaster.tecmint.com
The following output confirms that all looks good.
You can also achieve the same as the root user as shown
# puppet agent -t
To view available certificates on the Puppet Master node, execute the following command.
$ sudo /opt/puppetlabs/bin/puppetserver ca list --all
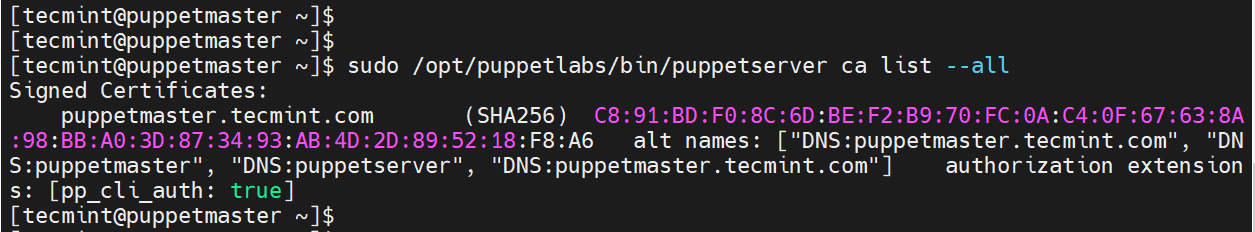
So far, we have managed to install Puppet Server and Agent on the Master node. If this is what you were looking for, then you are done and dusted.
However, we mentioned that Puppet works in a client-server architecture. In the following step, we will demonstrate how to install and configure the Puppet agent on the client node.
Step 11: Install and Configure Puppet Agent on Slave
In this section, we will install Puppet Agent on a Ubuntu Slave node and then establish communication between the Pupper Master node and the Client.
For Ubuntu 22.04
$ wget https://apt.puppetlabs.com/puppet7-release-jammy.deb $ sudo dpkg -i puppet7-release-jammy.deb $ sudo apt update $ sudo apt install puppet-agent -y
For Ubuntu 20.04
$ wget https://apt.puppet.com/puppet7-release-focal.deb $ sudo dpkg -i puppet7-release-focal.deb $ sudo apt update $ sudo apt install puppet-agent -y
Once installed, access the agent’s configuration file.
$ sudo vim /etc/puppetlabs/puppet/puppet.conf
Add the following section.
[main] server = puppetmaster.tecmint.com
Save the changes and exit.
To apply the changes, restart the Puppet agent service.
$ sudo systemctl restart puppet $ sudo systemctl enable puppet
Step 12: Connect Puppet Agent to Puppet Server
The last step is to establish a connection between the Puppet server and the agent installed on the client system. To do this, access the client node and generate certificates for the Pupper master to sign.
$ sudo /opt/puppetlabs/bin/puppet agent -t
You will get a notification that the certificate has not been signed yet.
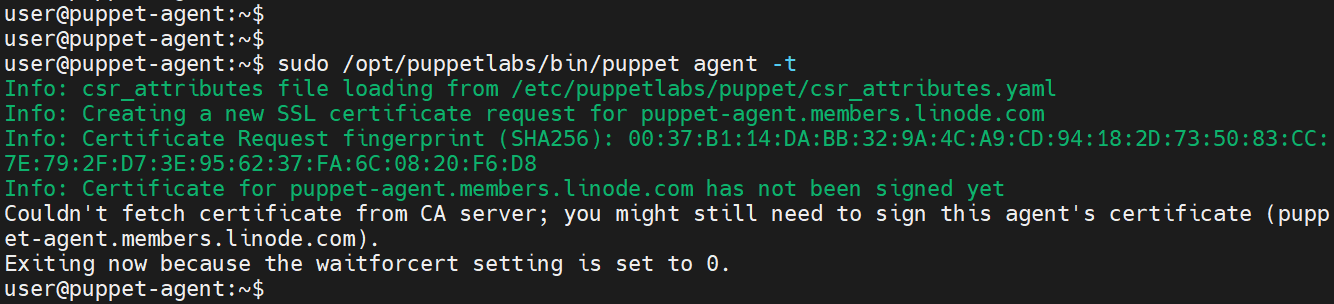
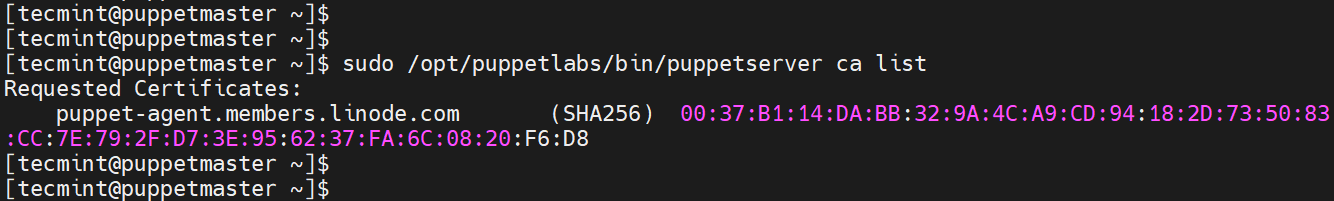
Head over to the Pupper master node and list the certificates that are pending to be signed. Here, the certificate is listed as puppet-agent.members.linode.com.
$ sudo /opt/puppetlabs/bin/puppetserver ca list
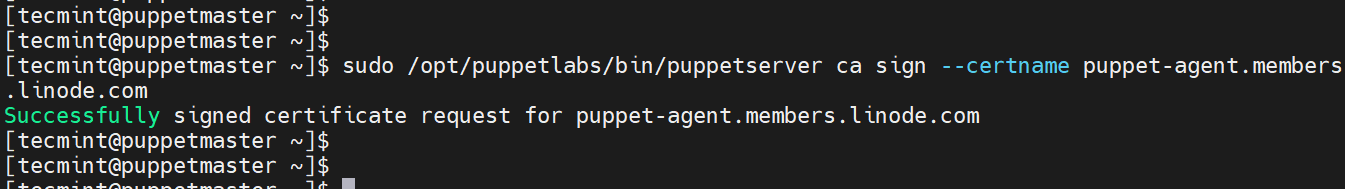
Now sign the certificate using the following command:
$ sudo /opt/puppetlabs/bin/puppetserver ca sign --certname puppet-agent.members.linode.com
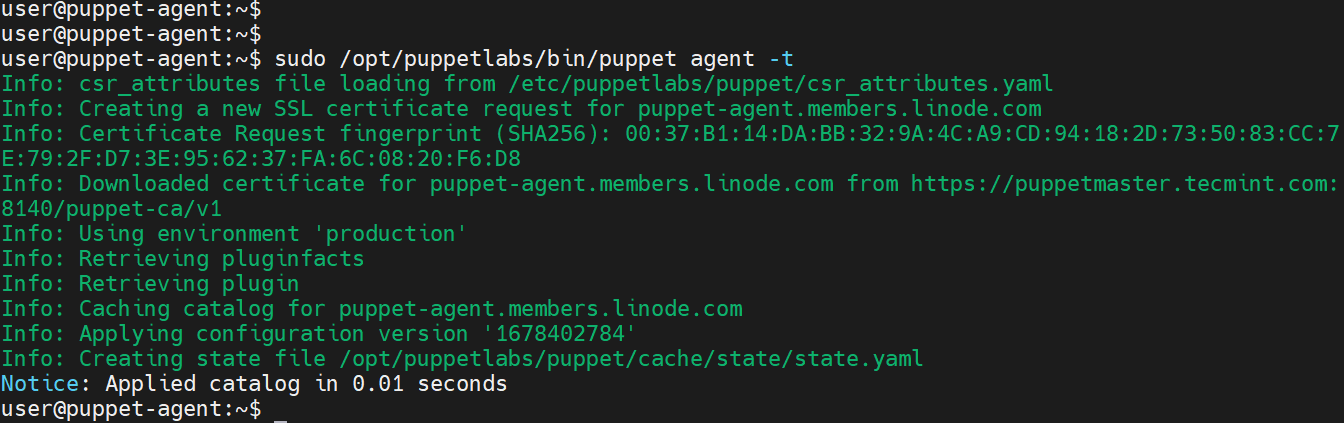
Finally, head back to the Client node and sign the certificate.
$ sudo /opt/puppetlabs/bin/puppet agent -t
Conclusion
This brings us to the end of this guide. In this article, we have demonstrated how to install Puppet Master and Agent on RHEL-based systems using Rocky Linux 8 nodes in our setup.





Hi Ravi,
I am getting the below error while generating a certificate in Master Server – CentOS
@Vamshidher,
I think you need to install libcrypt.so module by installing libxcrypt.