Everyone knows that Linux systems come with root user access and by default, root access is enabled for the outside world.
For security reasons, it’s not a good idea to have ssh root access enabled for unauthorized users. Because any hacker can try to brute force your password and gain access to your system.

So, it’s better to have another account that you regularly use and then switch to the root user by using the ‘su –‘ command when necessary. Before we start, make sure you have a regular user account and with that, you su or sudo to gain root access.
[ You might also like: How to Secure and Harden OpenSSH Server ]
In Linux, it’s very easy to create a separate account, log in as a root user and simply run the adduser command to create a separate user. Once the user is created, just follow the below steps to disable root login via SSH.
We use sshd master configuration file to disable root login and this will may decrease and prevent the hacker from gaining root access to your Linux box. We also see how to enable root access again as well as how to limit ssh access based on users’ list.
Disable SSH Root Login
To disable root login, open the main ssh configuration file /etc/ssh/sshd_config with your choice of editor.
# vi /etc/ssh/sshd_config
Search for the following line in the file.
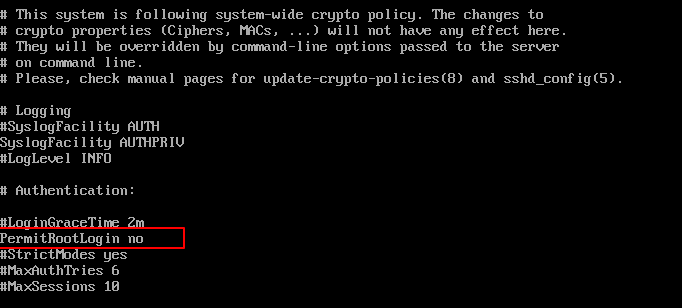
#PermitRootLogin no
Remove the ‘#‘ from the beginning of the line. Make the line look similar to this.
PermitRootLogin no
Next, we need to restart the SSH daemon service.
# systemctl restart sshd OR # /etc/init.d/sshd restart
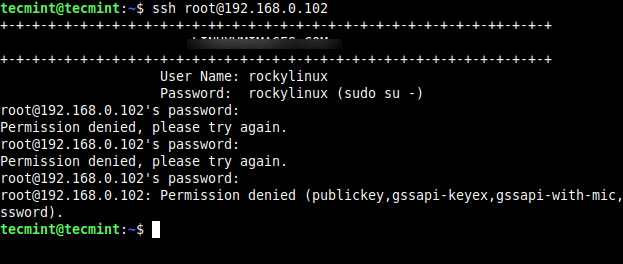
Now try to log in with the root user, you will get a “Permission denied” error.
$ ssh [email protected] [email protected]'s password: Permission denied, please try again.
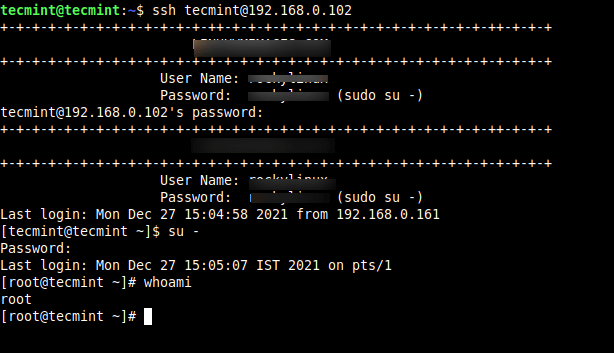
So, from now onwards login as a normal user and then use the ‘su’ command to switch to root user.
$ ssh [email protected] [email protected]'s password: Last login: Mon Dec 27 15:04:58 2021 from 192.168.0.161 $ su - Password: Last login: Mon Dec 27 15:05:07 IST 2021 on pts/1
Enable SSH Root Login
To enable ssh root logging, open the file /etc/ssh/sshd_config.
# vi /etc/ssh/sshd_config
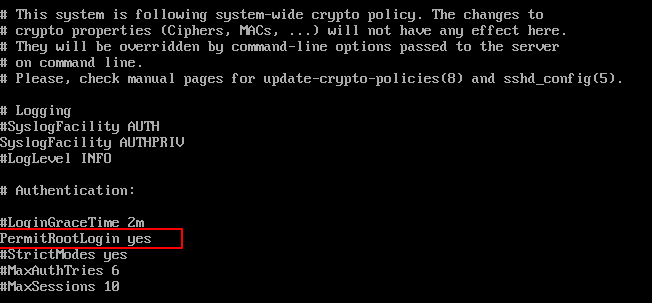
Search for the following line and remove the ‘#‘ at the beginning and save the file.
PermitRootLogin yes
Restart the sshd service.
# systemctl restart sshd OR # /etc/init.d/sshd restart
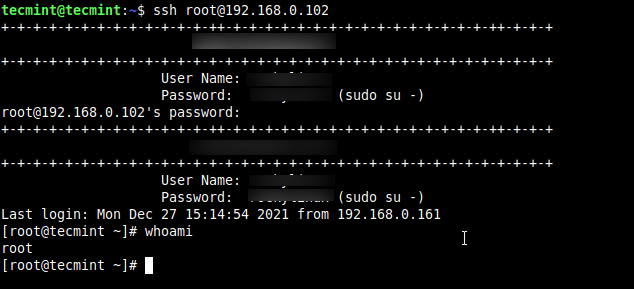
Now try to log in with the root user.
$ ssh [email protected] [email protected]'s password: Last login: Mon Dec 27 15:14:54 2021 from 192.168.0.161
Limit SSH User Logins
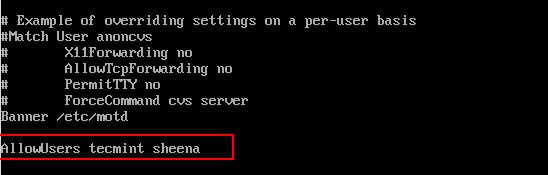
If you have a large number of user accounts on the systems, then it makes sense that we limit remote SSH access to those users who really need it. Open the /etc/ssh/sshd_config file.
# vi /etc/ssh/sshd_config
Add an AllowUsers line at the bottom of the file with a space separated by a list of usernames. For example, user tecmint and sheena both have access to remote ssh.
AllowUsers tecmint sheena
Now restart ssh service.





Open the sshd_config file.
add the following configuration.
and restart the sshd service with the following command.
It’s better and more save to use “screen” at the user-account.
and get back the session
also possible session with other names mylogin1, mylogin2, mylogin3 to have a multisession with 4/10 sessions over “screen”
test it out and good hack
best
Blackysgate
What does putting the ‘#‘ at the beginning actually do?
It comments that specific line/command.
I prefer creating an ssh group and add to that group and allowing that group on sshd_config, but well same goal achieved either way!
Great article!
Great article.