In order to protect sensitive data extraction from servers by users who have physical access to machines, it’s a best practice to disable all USB storage support in Linux kernel.
In order to disable USB storage support, we first need to identify if the storage driver is loaded into Linux kernel and the name of the driver (module) responsible with storage driver.
Run the lsmod command to list all loaded kernel drivers and filter the output via grep command with the search string “usb_storage”.
# lsmod | grep usb_storage
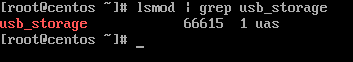
From lsmod command, we can see that the sub_storage module is in use by UAS module. Next, unload both USB storage modules from kernel and verify if the removal has been successfully completed, by issuing the below commands.
# modprobe -r usb_storage # modprobe -r uas # lsmod | grep usb
Next, list the content of the current runtime kernel usb storage modules directory by issuing the below command and identify the usb-storage driver name. Usually this module should be named usb-storage.ko.xz or usb-storage.ko.
# ls /lib/modules/`uname -r`/kernel/drivers/usb/storage/
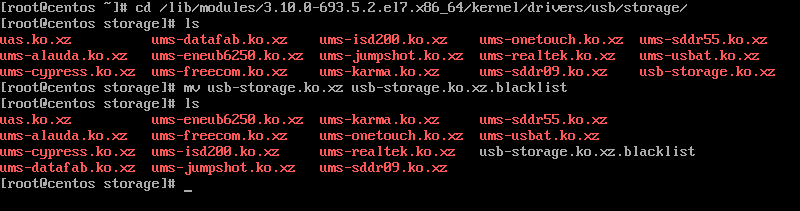
In order to block USB storage module form loading into kernel, change directory to kernel usb storage modules path and rename the usb-storage.ko.xz module to usb-storage.ko.xz.blacklist, by issuing the below commands.
# cd /lib/modules/`uname -r`/kernel/drivers/usb/storage/ # ls # mv usb-storage.ko.xz usb-storage.ko.xz.blacklist
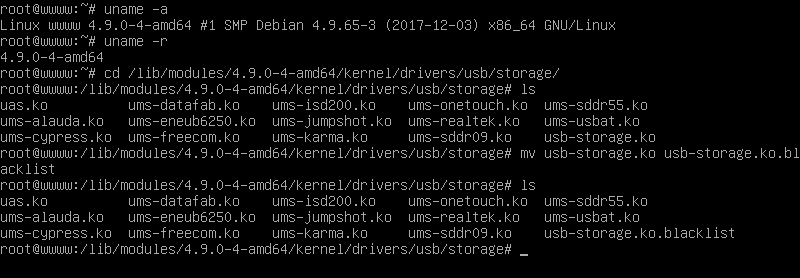
In Debian based Linux distributions, issue the below commands to block usb-storage module from loading into Linux kernel.
# cd /lib/modules/`uname -r`/kernel/drivers/usb/storage/ # ls # mv usb-storage.ko usb-storage.ko.blacklist
Now, whenever you plug-in a USB storage device, the kernel will be fail to load the storage device driver intro kernel. To revert changes, just rename the usb module blacklisted back to its old name.
# cd /lib/modules/`uname -r`/kernel/drivers/usb/storage/ # mv usb-storage.ko.xz.blacklist usb-storage.ko.xz
However, this method applies only to runtime kernel modules. In case you want to blacklist USB storage modules form all available kernels in the system, enter each kernel module directory version path and rename the usb-storage.ko.xz to usb-storage.ko.xz.blacklist.



Hi,
Is it possible to block USB ports in this way:
you can copy from USB do HDD, but you cannot copy from HDD to USB??
Thanks!!
I.
print(“Thanks”)
Hi this is karthik i have build the samba server and sharing files between 20 system how to get protected from users when they accessing it through pendrive.
usbguard has more fine-grained controls for usb devices. You can configure the service, and then any device which is not listed is blocked. It works so well that on the first couple of times I worked with it, it blocked my usb keyboard.
How about adding the following to modprobe blacklist?
Saves time and works regardless of kernel upgrades.
Also, disable usb authorization via /sys/bus/usb/devices/usbX/authorized and you’re good to go.
So after next kernel update you have to do same again either automatically or manually.
It would be easier to blacklist by using /etc/modprobe.d/blacklist-*.conf file.
But how about allowing only certain encrypted/locked USB storage devices? That’s bit more complicated by managing udev rules.
Thank you, I’m glad at least someone here has some sanity! Renaming modules?? whatever next??!!