GRand Unified Bootloader (GRUB) is a default bootloader in all Unix-like operating systems. As promised in our earlier article “How to reset a forgotten root password“, here we are going to review how to protect GRUB with passwords.
As mentioned earlier post, anyone can log in into single-user mode and may change system settings as needed. This is the big security flow. So, to prevent such unauthorized person to access the system we may require to have grub with password protected.
Here, we’ll see how to prevent users from entering into single user mode and changing the settings of systems that may have direct or physical access to the system.
Generate GRUB Bootloader Password
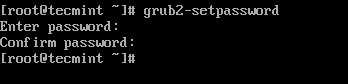
Create a password for GRUB, be a root user, and open the command prompt, type the below command.
# grub2-setpassword
When prompted type grub password twice and press enter.
This will generate a hashed GRUB bootloader password in the file /boot/grub2/user.cfg file and can be viewed using the cat command as shown.
# cat /boot/grub2/user.cfg
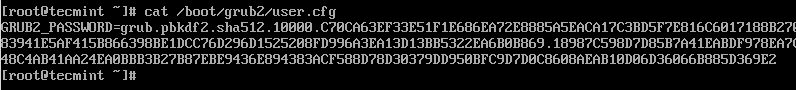
Recreate the GRUB Configuration File
After creating the GRUB password, you need to re-create the new GRUB configuration file by running the following command.
# grub2-mkconfig -o /boot/grub2/grub.cfg
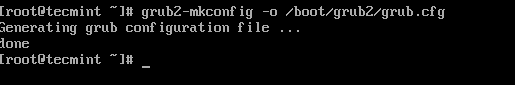
The above command will set the grub password in the configuration file. Now, reboot the system and check if the new GRUB password is set properly.
# reboot
Testing GRUB Password Protection
After your system restart, you will get the following GRUB screen, where you will get 5 seconds to break the normal boot process. So quickly press e key to breaking the boot process.
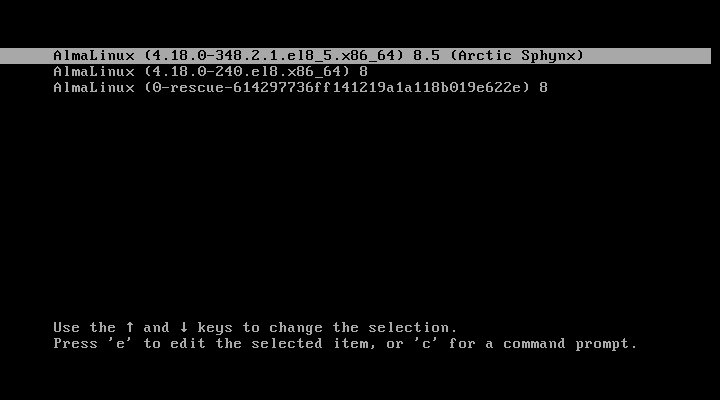
Once you press the e key it will prompt you to enter the GRUB password as shown.

After entering the right username and password, you can edit GRUB parameters as shown.
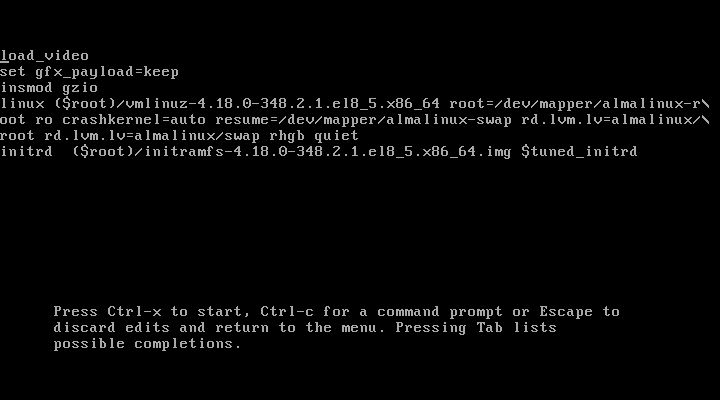
Removing GRUB Password Protection
To remove GRUB password-protect from boot menu, simply delete the file /boot/grub2/user.cfg.
# rm /boot/grub2/user.cfg
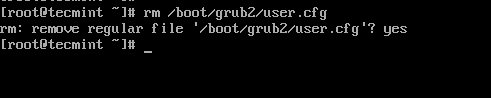
This is how we can protect GRUB with passwords. Let us know how do you secure your system? via comments.





Hi,
This article was helpful for me..
Thanks a lot
Excellent article
This will only protect the installed group, it’s still possible to boot up grub from a usb drive and then boot the Linux kernel in single-user mode from there.
But what about if you forbidden boot from USB?
Hi sir, this article was helpful, but terminal says grub command not found. What can be the issue?
What this equates to user commands ubuntu?
Thanks Alot
Hello , this was very help full for me
i have tried this it worked well and also i have tried removing the password in /etc/grub.conf file . i have doubt here if i forget the root password i will reset through single user mode . for suppose if i forget the password for both root and grub password . then hw can i recover it . please help me out in this
@Samanth,
Same way, go the the single user mode and remove the grub password from the grub menu configuration file and for resetting root password follow these guides.
https://www.tecmint.com/reset-forgotten-root-password-in-centos-7-rhel-7/
https://www.tecmint.com/reset-forgotten-root-password-in-rhel-centos-and-fedora/
@ravi Saive , thanks for the reply , actually my doubt is how can we enter into single user mode without providing the grub password . the e ( for edit ) it self is not shown there and only the ” p ” option is displaying. please let me know this . sorry for asking you the silly doubts i just want to clear my doubt . thanks in Advance .
@Samanth,
Sorry for my last comment, actually you can’t switch to single user mode when grub is password protected, the only way is to recover is using Linux Live CD. Boot into Linux using Linux Live CD, mount the root partition in rw mode and remove the password in the grub configuration file…
thank a lot, thank for the support @ravi Saive.